Learn
Human & Machine
Giving AI cybersecurity the human touch.
Quick view
Overview
In a world rife with cyber threats and attacks, organizations are constantly seeking innovative solutions to protect themselves.
Human-machine collaboration could be the winning combination for improving cybersecurity you’ve been looking for. By reducing risks, optimizing response time, and effectively utilizing SOC skills, enterprises can stay ahead of the curve in the ever-evolving landscape of cyber threats.
New challenges need new solutions.
The increasing dependency on digitization, Internet-of-Things (IoT), open-source software, and cloud computing has created unique challenges for protecting networks, systems, and applications against malicious attacks and novel evasion techniques that can evade existing detection mechanisms.
Complementing and augmenting human capabilities with Artificial Intelligence (AI) technology is vital for building resilient threat defense solutions that safeguard against advanced persistent threats (APTs) and zero-day attacks, help our customers better manage risks, and improve operating efficiency in rapidly evolving cyber environments.
of organizations use IoT
of organizations have detected IoT-based attacks
IoT connections by 2025
Source: Gartner. IoT Security Primer: Challenges and Emerging Practices. https://emtemp.gcom.cloud/ngw/globalassets/en/doc/documents/355851-iot-security-primer-challenges-and-emerging-practices.pdf
The weaknesses of IDS.
The exponential rise in the number and diversity of contemporary cyber-attacks creates a significant challenge for traditional signature-based intrusion detection solutions (IDS), which rely on threat history data to block and remediate future malicious attacks proactively. While these misuse detection solutions offer high detection accuracy and low false positive rates, keeping their signature databases current is costly. It has an alarmingly low zero-day attack detection rate since these attacks exploit unknown vulnerabilities, and their signatures do not exist in the repository.
Another type of IDS uses anomaly detection techniques that look for suspicious events that deviate from regular user or entity behavioral thresholds. Since anomaly detection asserts that any outliers outside predefined limits are symptoms of a cyberattack, their premise is detecting previously unseen cyberattacks. However, their performance and practical use for SIEM and incident response is limited since they suffer from generating a high rate of false positives on benign activity, needlessly creating unplanned work, and wasted effort.
Cisco argues that “Few tasks in security are more tedious than vulnerability management and triaging countless false positives”.1 A research study by Critical Start on the Impact of Security Alert Overload of SOC found that almost 50% of SOC teams reported a false-positive security alert rate of 50% or higher, and 35% of SOC teams had an annual staff turnover rate greater than 25%.2
- Security Outcomes Study, Volume 1 (https://www.criticalstart.com/wp-content/uploads/CS_MDR_Survey_Report.pdf)
- The Impact of Security Alert Overload of SOC. (https://www.criticalstart.com/wp-content/uploads/CS_MDR_Survey_Report.pdf)
Verimatrix’s hybrid solution:
the best of both worlds
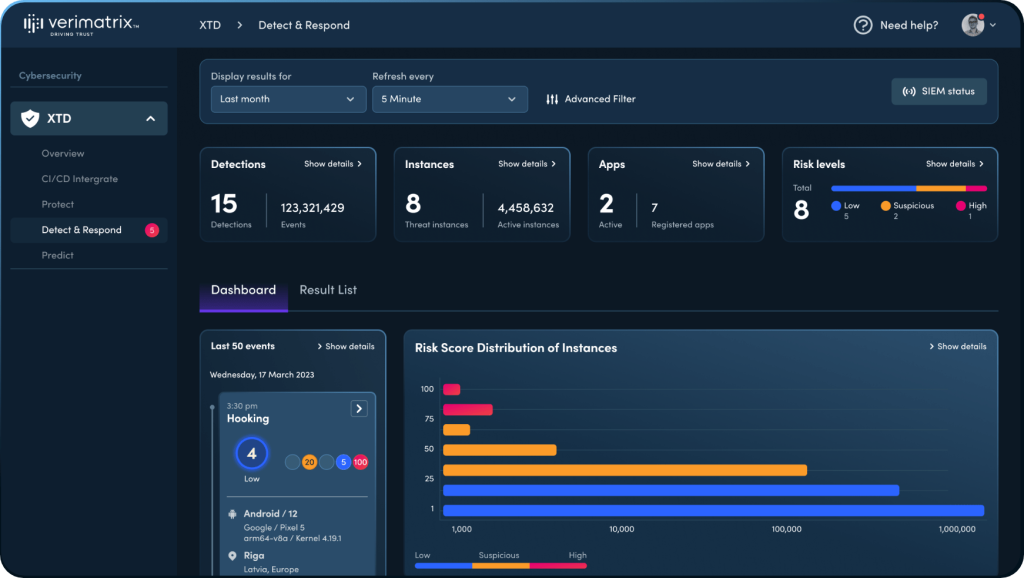
Given the limitations of traditional intrusion detection systems, we invested in the research and development of an Artificial Intelligence (AI) powered XTD solution. The result of this work has shown the potential to accurately detect known CVEs, new novel attacks designed to subvert systems using previously unseen methods, offer improved response times, and avoid excessive false alarms and other diminishing effects. AI is more adept at performing repetitive and routine tasks and rapidly unearthing valuable hidden insights in massive amounts of structured or unstructured data than humans. They continuously learn and adapt as they interact with cyberattacks and the cybersecurity environment. Organizations that leverage cyber threat intelligence are twice as likely to succeed in detection and response capabilities compared to non-intelligence users. 3
Under some circumstances, it is appropriate to employ autonomous AI to cope with the frequency and velocity of network events. However, our view is that an overreliance on machine algorithms and the absence of human oversight and retrospective analysis can lead to a situation where skilled adversaries can penetrate system defenses and carry out destructive activities.
3. Security Outcomes Study, Volume 2. https://www.cisco.com/c/dam/en/us/products/collateral/security/security-outcomes-study-vol-2-report.pdf
A collaborative approach.
Collaborative or augmented threat intelligence rather than autonomous AI to monitor and control the behavior of sophisticated systems and networks can achieve more robust detection, response, and remediation results. Gartner describes this symbiotic combination of human and machine as “a human-centered partnership model of people and AI working together to enhance cognitive performance”.4
Verimatrix’s hybrid ML-based IDS solution builds upon the principle of complementing and augmenting your SOC workforce capabilities, enabling the seamless knowledge exchange between machines, cybersecurity professionals, data scientists, and subject matter experts, creating more effective teams.
4. Gartner. IoT Security Primer: Challenges and Emerging Practices. https://emtemp.gcom.cloud/ngw/globalassets/en/doc/documents/355851-iot-security-primer-challenges-and-emerging-practices.pdf
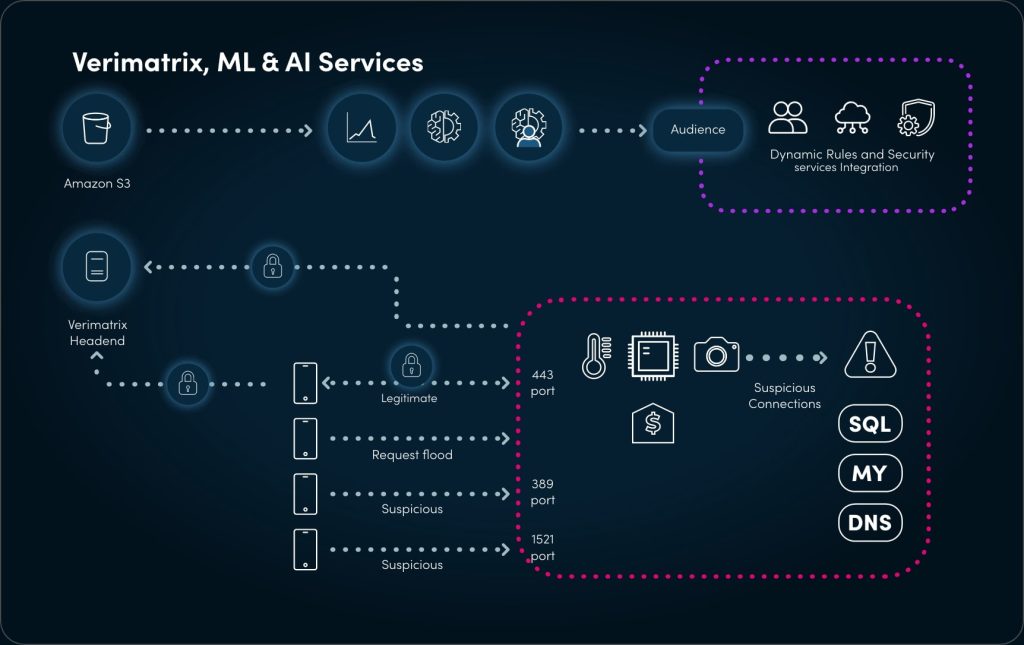
Verimatrix’s collaborative, human-centered AI allows our customers to manage AI risks, optimize response times, mitigate avoidable bias and illuminate blind spots by complementing technology with human instincts and common sense.”
– Matthew Fite, CTO at Verimatrix
2023 Gold Award Winner

Security
The benefits of utilizing both AI/ML and human professionals.
5. Security Outcomes Study, Volume 1. https://www.criticalstart.com/wp-content/uploads/CS_MDR_Survey_Report.pdf
Human & machine capabilities: better together
Collaborative threat intelligence radically changes the way SIEM work gets done and amplifies the capabilities of the SOC workforce. Security functions that depend on intensive human labor and face barriers to improvement due to poor scalability may benefit significantly from human-centric XTD, which is designed to streamline and simplify the interaction between human and machine.
Humans augment machines by:
Ensuring precision
Training and evaluating threat intelligence models detecting known and new attacks ensuring high precision and recall.
Providing clarity
Explain AI-detected cybersecurity incidents to our customers, especially for regulatory purposes, and where the results may be counterintuitive or controversial.
Ensuring safety and compliance
Continually ensure that intelligent agents operate accurately, safely, and responsibly when human judgment is needed.
Machines enhance what humans do by:
Finding solutions with ease
Boosting analytics and problem-solving skills within rapidly evolving environments.
Improving customer interactions
Enabling organizations to interact with their customers in creative and effective ways.
Continuously optimizing
Ensure the continuous improvement of the speed and accuracy of threat detection.
A bright future:
Providing AI transparency
Allow the team to understand what influenced its behavior, build trust in their decisions, make better recommendations, and confirm they meet regulatory requirements.
Offering what-if capabilities
Estimate how the AI outcome will change when different threat scenarios are fed into the AI model.
Construct security response actions
Simulate various intervention scenarios and create rules to determine which users or entities will benefit from an intervention.
Verimatrix’s approach to AI/ML
Employ deep learning
Detect abnormal behaviors, generate new predictors and anomaly scores for flows at the port level.
Implement advanced ML
Utilize ensemble machine learning algorithms to accurately detect attacks and estimate the type of attack.
Use correlation mechanisms
Help with early intervention responses by reasoning and correlating multi-stage attack plans based on security states of our customer’s systems and networks.
Use local and global explainable AI (XAI) tools
Provide interpretable representations of the system’s advanced black-box predictive models that replace latent and less reliable rule-based or signature-based approaches.
Threat patterns Verimatrix can detect:
Verimatrix’s ML model is highly successful in predicting benign and malicious botnet, IoT network activities for 20 attack types from diverse range of networks, applications, and protocols with different topologies.
Verimatrix efficiently and accurately classifies benign flows and malicious flows for known
How this benefits a CISO or SOC team.
Proactive protection
Provides more robust and timely proactive protection against vulnerability exploits to disrupt attacks in their early stages compared to traditional solutions.
Threat identification
Enable SOC teams to determine malicious intent with high confidence.
Improved risk management and reduced costs
Provides improved response times and avoids excessive false alarms and other diminishing effects.
Optimized workflow
Relieves SOC specialists of mundane tasks, enabling them to focus on enjoyable and valuable work, and mitigate avoidable bias and blind spots.
Incorporated human judgment
Complements cyber security technology with human instincts and judgment.
Shortened cybersecurity interventions
Builds trust in their decisions, makes better recommendations, and verifies that they meet regulatory requirements.
Zero-day attack mitigation
Minimize the reliance on manual detection methods to improve speed of detection.
Improved staff welfare
Offers a competitive advantage in the day-to-day execution of minimizing staff burnout.
Detecting what others can’t.
- Offers more robust protection with high recall (lower false positive alarms) against ‘zero-day’ attacks than commonly used signature-based and anomaly-based cybersecurity detection tools. Zero-day attacks avoid detection and gain unauthorized access to a system by exploiting yet to be discovered vulnerabilities.
- AI detects patterns humans cannot see, and it continuously learns and adapts as it interacts with cyberattacks and the cybersecurity environment.
- Our threat intelligence is adept at detecting new attacks through user and entity behavior analytics (UEBA) techniques. It creates and examines the features of an attack plan based on its interactions with the target system to predict whether it will result in a malicious outcome, rather than examining the signature of an incoming flow.
When Verimatrix’s human staff step in.
Detecting and responding to complex, multi-stage attacks require integrating Verimatrix XTD AI pipelines into existing security analysis and operations workflows.
Verimatrix Data Scientists perform statistical analysis, causal inference, supervised and unsupervised learning, and deep learning techniques to translate cyber and network security related requirements into sophisticated models to defend against cyber-attacks and to help derive new insights.
Domain knowledge experts, decision-makers, and data scientists in collaborative AI environments work together to continuously:
• Understand diverse on-going attacks and attack patterns by analyzing the security market, security trends, event logs, and behavior of the clients.
• Feed the external knowledge by continuously training and optimizing the machine learning models from lessons learned, changes in the cyber security environment, customer feedback, and new regulations.
• Develop and finetune dynamic rules and ML-based intervention automation.
• Continuously enhance or adjust ML models to adapt to nuances across different use cases, geographies, industries, topologies, protocols, applications, and users.
• Continuously monitor, evaluate, and take corrective actions when the statistical properties of the predictors used to make predictions change over time.
• Explain AI-detected cybersecurity incidents to non-experts, especially for regulatory purposes, and where the results may be counterintuitive or controversial.
• Continually ensure that intelligent agents operate accurately and responsibly when human judgment is needed.
Final thoughts
Integrating human and machine threat intelligence enhances security by reducing AI risks, optimizing response time, and utilizing SOC skills effectively. Humans remain critical in threat identification and mitigation, complementing machine automation and intelligence. As security threats evolve, companies that quickly adapt and respond to emerging threats gain a competitive edge. Collaborative human and machine threat intelligence is a cost-effective and practical solution for staying ahead in the fight against cybercrime.
Talk to Us
Ready to deploy powerful protection to your applications? Submit the form and a Verimatrix representative will contact you to schedule a product demo, explain our pricing, and get you started on a free trial.
With Verimatrix XTD you can:
- Shield mobile applications in minutes
- Easily integrate into your development workflows
- Effectively manage risk and meet compliance obligations











