Learn
Zero Trust, Zero Compromise
Learn how XTD continuously validates connections for better security.
Overview
Zero trust is an increasingly discussed topic within the cybersecurity industry and has changed the way many security professionals look at how they can defend their organizations.
The question arises: how do you utilize zero trust when protecting your business from the threats posed by connected apps and unmanaged devices? Verimatrix XTD has the solution.
What is zero trust?
In the past, cybersecurity professionals generally believed that everything outside of their organization’s network perimeter was a threat while everything within the perimeter was harmless. With the dramatic changes in the way we work and the technology we use, this way of thinking has become increasingly outdated.
The explosion in popularity of mobile apps used on millions of connect consumer devices have transformed the attack surface. The enterprise defense perimeter is no longer as secure as it once was, since unmanaged consumer devices are given permission to communicate and share data with the enterprise (via apps). In the event of am attacker gaining access to the network, they could gain the ability to navigate access company resources, execute ransomware attacks or steal sensitive information.
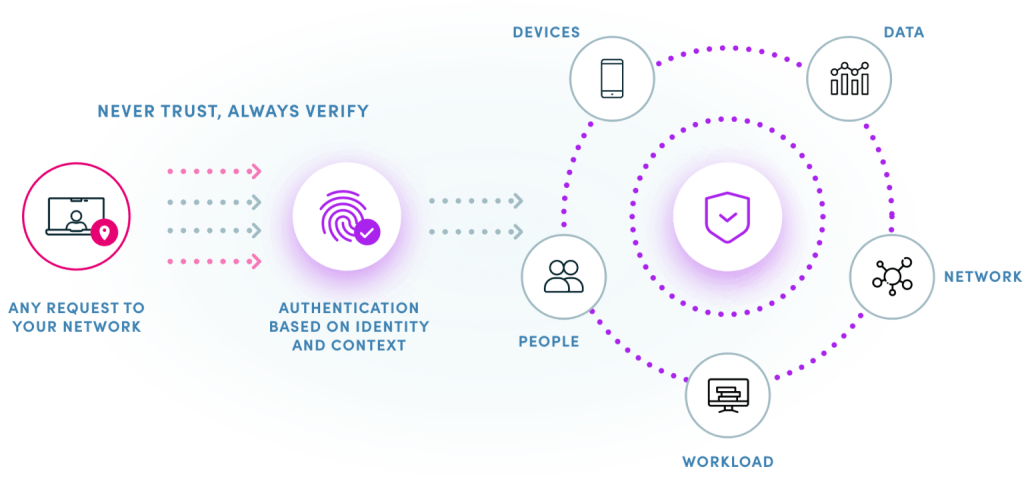
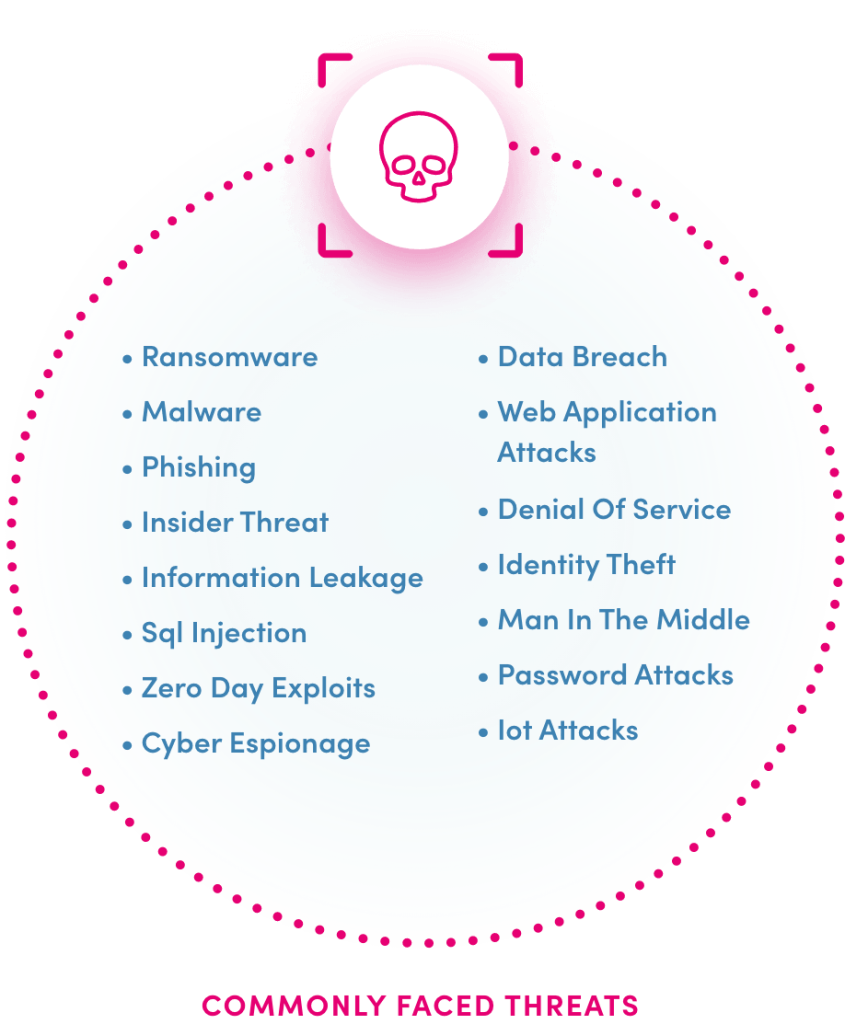
An evolving threat landscape.
Often, they show too many alerts making it hard for the user to know what to focus on and in a lot of cases they require full-time resources to support them. This can be expensive for little in the way of reward.
The zero trust reality.
Fortunately, there are alternatives available that are far better suited to the modern fast-paced environments many security professionals now face. Many cybersecurity companies are racing to push their zero trust products onto the market but as is often the way in this industry, there are some who promise that their product ‘can do it all’.
If a cybersecurity company makes that claim, then run in the opposite direction as there is no such thing! Instead, a variety of tools and services are required to cover all the pillars of the zero-trust approach.
What is Verimatrix XTD (Extended Threat Defense)?

Verimatrix XTD is a zero code cybersecurity solution that closes the open door in most enterprise security walls by protecting the mobile apps and unmanaged devices that connect to it.
With IT teams putting the bulk of their focus on desktop infrastructure, they can forget to cover the security blind spots created by mobile apps and unmanaged devices connected to the corporate network. Hackers are always looking for easy targets, so they have shifted their focus to unmanaged devices that are often unpatched and are not protected with complex passwords. Once they connect to such devices, they can then easily penetrate the network.
With Verimatrix XTD, you can monitor these threats at the endpoint and act before the bad guys compromise your enterprise.
Verimatrix XTD can help and become one of the foundations in achieving an overall zero trust strategy of an enterprise or financial institution as well as help CISOs and security strategists close any security gaps caused by connected mobile apps and unmanaged devices.
The pillars XTD covers are:
Assume breach and always verify
XTD collects data from devices and feeds it back so that it can detect anomalies in a compromised app or unmanaged device allowing a user to take a proactive approach by detecting breaches well in advance.

Just in time access
Based on the risk posture of an organization’s Connected Apps and Unmanaged devices XTD can provide the information/signals to the back-end services so that an administrator can allow or deny access or an ongoing transaction. XTD can also guide the backend services to provide restricted/limited/full access to corporate resources.

Defense in depth
Based on the device security risk status, XTD advises financial/customer services to collect additional factors for authentication prior to network access or a financial transaction. Factors such as something you know, something you are and something you have.

Minimize blast radius
XTD can help prevent the network's lateral movement and attack kill chain by shutting down a compromised or vulnerable device well in advance, minimize the blast radius of an attack.
Least privilege
XTD can help an administrator determine whether they should grant the least privilege access or the greatest privilege access to the network or specific resource. XTD can help backend services apply strict IAM/network policies during just in time access.
Talk to Us
Ready to deploy powerful protection to your applications? Submit the form and a Verimatrix representative will contact you to schedule a product demo, explain our pricing, and get you started on a free trial.
With Verimatrix XTD you can:
- Shield mobile applications in minutes
- Easily integrate into your development workflows
- Effectively manage risk and meet compliance obligations











