Streaming digital content—such as series, movies, and sports—wherever, whenever, and on whatever device is the world consumers live in today. However, this convenience poses a significant challenge for sports rights holders and content distributors: piracy.
For sports streaming services, piracy isn’t just a nuisance. It’s a major revenue threat that can erode profits, harm the sports ecosystem, and diminish content rights’ value. Building a secure, smooth-running streaming service requires meticulous planning with integrated, multi-layered security measures.
Pirates will target the weakest links in the streaming ecosystem, so closing security gaps demands complex solutions, including protocols and integrations from multiple vendors. A multi-defense approach—incorporating DRM, forensic watermarking, app shielding, and threat monitoring—is essential to protect today’s content effectively.
I believe that working with experienced technical partners is crucial to implementing such defenses. Partners can provide specialized knowledge and ensure seamless integration across diverse platforms, helping to secure the live-streaming infrastructure against piracy threats.
This article outlines a checklist of key measures every streaming operator should consider before and during a live sports event to ensure a secure, professional experience.
Technical overview: How streaming content works for a live sports event
Streaming a live sports event involves capturing the video feed from the live event, encoding it into digital media files, and then distributing it to viewers over the internet.
Here’s an overview of the main steps:
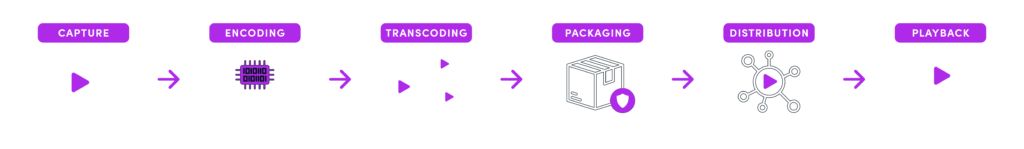
- Capture: Cameras at the event capture the live video feed, which is sent to a processing unit.
- Encoding: The edited video feed is compressed and encoded into a digital format suitable for streaming. This step reduces file size and ensures compatibility with a wide range of devices. The encoder divides the feed into chunks (segments) and applies codecs like H.264 or H.265 for video and AAC or MP3 for audio.
- Transcoding: The encoded content is converted into multiple quality levels (resolutions and bitrates) to allow for adaptive streaming, where the video quality dynamically adjusts based on the viewer’s internet speed.
- Packaging: The content is packaged into streamable formats (e.g., HLS or DASH), which split the video into small segments and add metadata, ensuring smooth playback across different devices.
- Distribution: The packaged content is sent to a Content Delivery Network (CDN), which caches and distributes it across various geographic locations. This reduces latency and improves streaming performance for viewers around the world.
- Playback: Viewers access the stream through the app on their device. The app requests the best quality segment from the CDN based on network conditions and device capabilities, and the segments are buffered and played back in real-time.
Checklist for preventing streaming content theft
In live sports, timing is of essence. Once the event is finished, the content value evaporates. Hence, protecting live-streamed sports events requires proactive, layered security measures to keep content safe from unauthorized distribution.
To simplify things, the following 10-step checklist highlights essential steps to prevent streaming content theft and keep live-streamed sports events safe from unauthorized distribution.
- Deploy app shielding & threat defense
The application lives in the hands of the pirate. Implement app shielding and threat defense solutions to protect your streaming app from tampering, reverse engineering, and malicious attacks.
These tools prevent unauthorized code modifications, secure the app environment, and stop reverse engineering the communication between the app and the streaming services.
- Encryption and secure transport
Use secure protocols like HTTPS and Secure Real-time Transport Protocol (SRTP) throughout the content delivery chain to minimize interception and person-in-the-middle attacks.
- Implement DRM protection
The content sources are meant to be easily accessible, so make sure the content is encrypted and keys are not easily captured.
Ensure that Digital Rights Management (DRM) like Widevine, FairPlay, or PlayReady is enabled on all content to control access and prevent unauthorized copying and playback.
- Tokenized access control
Pirates are thirsty for access points. Use access tokens with short expirations to ensure only authorized users can access the stream and the sharing is minimized.
- Geofencing and IP restrictions
Protect your IP by avoiding easy access to non-license sites. Set geographic and IP restrictions to limit access based on licensing agreements, preventing unauthorized viewing from restricted regions or VPNs.
- Monitor for credential sharing and usage patterns
Credential sharing has gone from friendly sharing to an abusive business model. Track unusual login patterns that might indicate account sharing or credential theft, such as multiple logins from different locations.
- Real-time piracy monitoring
The web is full of sources of pirate content, particularly known forums. Deploy anti-piracy services to regularly monitor social media, forums, and piracy sites for unauthorized streams or links to the live event.
- Protect the DRM communication E2E
Hackers know that standard secure communications are not always secure. On top of secure protocols (i.e., https), introduce extra security communication protection to the DRM licenses to ensure the secure communication is only terminated at the allowed secured application—protected end-to-end—completely avoiding person-in-the-middle attacks.
- Enable forensic watermarking
When everything fails and content still gets leaked, forensic watermarking is the way. Use forensic watermarking to insert invisible, session-specific watermarks into the stream, allowing traceability if pirated content surfaces online.
- Use multi-factor authentication (MFA)
Credential theft is always on the menu; hackers can impact your users’ privacy. Add an extra layer of security with MFA, ensuring that users verify their identity before accessing the stream.
Bringing it home
The sports industry relies on reaching a vast audience. To achieve this, sports providers strive to make their broadcasting rights as accessible as possible. However, this accessibility means that security measures can vary between providers, leaving a sport vulnerable to the weakest security link among them.
Implementing professional-grade content protection and anti-piracy measures is not optional—they’re critical for success. Properly securing live content requires not only sophisticated tools but also thorough planning and collaboration with technical experts who understand the complexities of the streaming ecosystem.
As the industry continues to innovate, building a strong defense to prevent streaming content theft is essential to protect revenue, maintain viewer trust, and uphold content rights.
By following the checklist above and working with the right integration partners, streaming operators can create a secure environment that minimizes piracy risks, ensuring that fans get the live, high-quality experience they expect—while the service retains control over its valuable content.




